// Tutorial //
How To Install and Secure phpMyAdmin on Ubuntu 20.04

Not using Ubuntu 20.04?Choose a different version or distribution.
An earlier version of this tutorial was written by Brennan Bearnes.
Introduction
While many users need the functionality of a database management system like MySQL, they may not feel comfortable interacting with the system solely from the MySQL prompt.
phpMyAdmin was created so that users can interact with MySQL through a web interface. In this guide, we’ll discuss how to install and secure phpMyAdmin so that you can safely use it to manage your databases on an Ubuntu 20.04 system.
1-Click deploy a database using DigitalOcean Managed Databases. Let DigitalOcean focus on scaling, maintenance, and upgrades for your database.
Prerequisites
In order to complete this guide, you will need:
- An Ubuntu 20.04 server. This server should have a non-root user with administrative privileges and a firewall configured with
ufw. To set this up, follow our initial server setup guide for Ubuntu 20.04. - A LAMP (Linux, Apache, MySQL, and PHP) stack installed on your Ubuntu 20.04 server. If this is not completed yet, you can follow this guide on installing a LAMP stack on Ubuntu 20.04.
Additionally, there are important security considerations when using software like phpMyAdmin, since it:
- Communicates directly with your MySQL installation
- Handles authentication using MySQL credentials
- Executes and returns results for arbitrary SQL queries
For these reasons, and because it is a widely-deployed PHP application which is frequently targeted for attack, you should never run phpMyAdmin on remote systems over a plain HTTP connection.
If you do not have an existing domain configured with an SSL/TLS certificate, you can follow this guide on securing Apache with Let’s Encrypt on Ubuntu 20.04. This will require you to register a domain name, create DNS records for your server, and set up an Apache Virtual Host.
Step 1 — Installing phpMyAdmin
You can use APT to install phpMyAdmin from the default Ubuntu repositories.
As your non-root sudo user, update your server’s package index:
- sudo apt update
Following that you can install the phpmyadmin package. Along with this package, the official documentation also recommends that you install a few PHP extensions onto your server to enable certain functionalities and improve performance.
If you followed the prerequisite LAMP stack tutorial, several of these modules will have been installed along with the php package. However, it’s recommended that you also install these packages:
php-mbstring: A module for managing non-ASCII strings and convert strings to different encodingsphp-zip: This extension supports uploading.zipfiles to phpMyAdminphp-gd: Enables support for the GD Graphics Libraryphp-json: Provides PHP with support for JSON serializationphp-curl: Allows PHP to interact with different kinds of servers using different protocols
Be aware that if you’re using a version of PHP other than the default one installed in the prerequisite LAMP stack tutorial, you will need to install the appropriate versions of these module packages. For instance, if you’re using PHP version 8.0, you will need to install the php8.0-mbstring package instead of the default php-mbstring package.
Run the following command to install these packages onto your system. Please note, though, that the installation process requires you to make some choices to configure phpMyAdmin correctly. We’ll walk through these options shortly:
- sudo apt install phpmyadmin php-mbstring php-zip php-gd php-json php-curl
Here are the options you should choose when prompted in order to configure your installation correctly:
- For the server selection, choose
apache2
Warning: When the prompt appears, “apache2” is highlighted, but not selected. If you do not hit SPACE to select Apache, the installer will not move the necessary files during installation. Hit SPACE, TAB, and then ENTER to select Apache.
- Select
Yeswhen asked whether to usedbconfig-commonto set up the database - You will then be asked to choose and confirm a MySQL application password for phpMyAdmin
Note: Assuming you installed MySQL by following Step 2 of the prerequisite LAMP stack tutorial, you may have decided to enable the Validate Password plugin. As of this writing, enabling this component will trigger an error when you attempt to set a password for the phpmyadmin user:
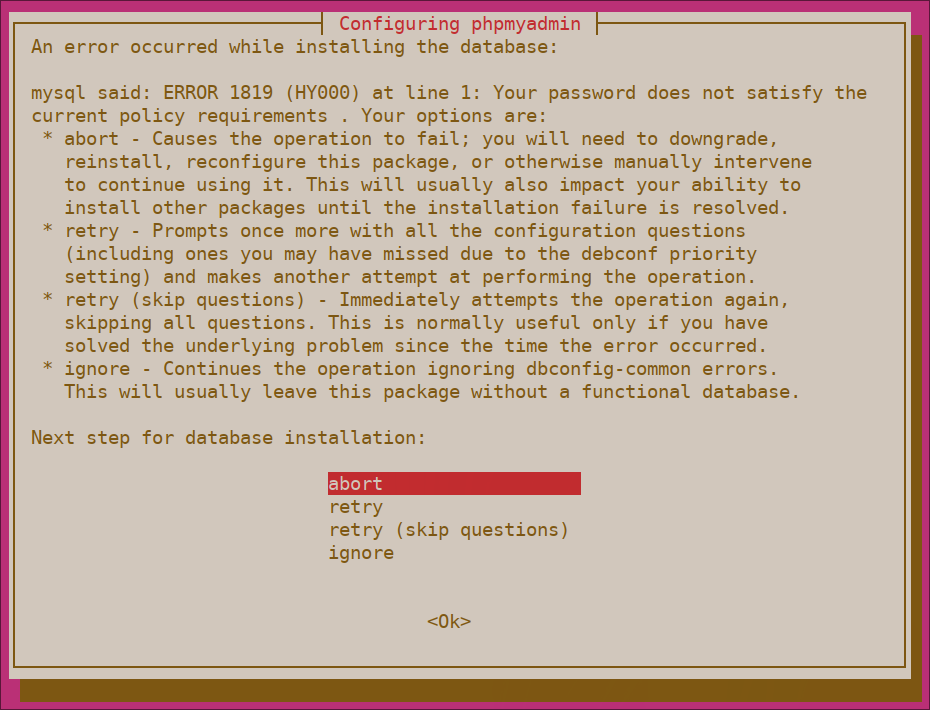
To resolve this, select the abort option to stop the installation process. Then, open up your MySQL prompt:
- sudo mysql
Or, if you enabled password authentication for the root MySQL user, run this command and then enter your password when prompted:
- mysql -u root -p
From the prompt, run the following command to disable the Validate Password component. Note that this won’t actually uninstall it, but just stop the component from being loaded on your MySQL server:
- UNINSTALL COMPONENT "file://component_validate_password";
Following that, you can close the MySQL client:
- exit
Then try installing the phpmyadmin package again and it will work as expected:
- sudo apt install phpmyadmin
Once phpMyAdmin is installed, you can open the MySQL prompt once again with sudo mysql or mysql -u root -p and then run the following command to re-enable the Validate Password component:
- INSTALL COMPONENT "file://component_validate_password";
The installation process adds the phpMyAdmin Apache configuration file into the /etc/apache2/conf-enabled/ directory, where it is read automatically. To finish configuring Apache and PHP to work with phpMyAdmin, the only remaining task in this section of the tutorial is to is explicitly enable the mbstring PHP extension, which you can do by typing:
- sudo phpenmod mbstring
Afterwards, restart Apache for your changes to be recognized:
- sudo systemctl restart apache2
phpMyAdmin is now installed and configured to work with Apache. However, before you can log in and begin interacting with your MySQL databases, you will need to ensure that your MySQL users have the privileges required for interacting with the program.
Step 2 — Adjusting User Authentication and Privileges
When you installed phpMyAdmin onto your server, it automatically created a database user called phpmyadmin which performs certain underlying processes for the program. Rather than logging in as this user with the administrative password you set during installation, it’s recommended that you log in as either your root MySQL user or as a user dedicated to managing databases through the phpMyAdmin interface.
Configuring Password Access for the MySQL Root Account
In Ubuntu systems running MySQL 5.7 (and later versions), the root MySQL user is set to authenticate using the auth_socket plugin by default rather than with a password. This allows for some greater security and usability in many cases, but it can also complicate things when you need to allow an external program — like phpMyAdmin — to access the user.
In order to log in to phpMyAdmin as your root MySQL user, you will need to switch its authentication method from auth_socket to one that makes use of a password, if you haven’t already done so. To do this, open up the MySQL prompt from your terminal:
- sudo mysql
Next, check which authentication method each of your MySQL user accounts use with the following command:
- SELECT user,authentication_string,plugin,host FROM mysql.user;
Output+------------------+-------------------------------------------+-----------------------+-----------+
| user | authentication_string | plugin | host |
+------------------+-------------------------------------------+-----------------------+-----------+
| root | | auth_socket | localhost |
| mysql.session | *THISISNOTAVALIDPASSWORDTHATCANBEUSEDHERE | caching_sha2_password | localhost |
| mysql.sys | *THISISNOTAVALIDPASSWORDTHATCANBEUSEDHERE | caching_sha2_password | localhost |
| debian-sys-maint | *8486437DE5F65ADC4A4B001CA591363B64746D4C | caching_sha2_password | localhost |
| phpmyadmin | *5FD2B7524254B7F81B32873B1EA6D681503A5CA9 | caching_sha2_password | localhost |
+------------------+-------------------------------------------+-----------------------+-----------+
5 rows in set (0.00 sec)
In this example, you can see that the root user does in fact authenticate using the auth_socket plugin. To configure the root account to authenticate with a password, run the following ALTER USER command. Be sure to change password to a strong password of your choosing:
- ALTER USER 'root'@'localhost' IDENTIFIED WITH caching_sha2_password BY 'password';
Note: The previous ALTER USER statement sets the root MySQL user to authenticate with the caching_sha2_password plugin. Per the official MySQL documentation, caching_sha2_password is MySQL’s preferred authentication plugin, as it provides more secure password encryption than the older, but still widely used, mysql_native_password.
However, some versions of PHP don’t work reliably with caching_sha2_password. PHP has reported that this issue was fixed as of PHP 7.4, but if you encounter an error when trying to log in to phpMyAdmin later on, you may want to set root to authenticate with mysql_native_password instead:
- ALTER USER 'root'@'localhost' IDENTIFIED WITH mysql_native_password BY 'password';
Then, check the authentication methods employed by each of your users again to confirm that root no longer authenticates using the auth_socket plugin:
- SELECT user,authentication_string,plugin,host FROM mysql.user;
Output+------------------+-------------------------------------------+-----------------------+-----------+
| user | authentication_string | plugin | host |
+------------------+-------------------------------------------+-----------------------+-----------+
| root | *DE06E242B88EFB1FE4B5083587C260BACB2A6158 | caching_sha2_password | localhost |
| mysql.session | *THISISNOTAVALIDPASSWORDTHATCANBEUSEDHERE | caching_sha2_password | localhost |
| mysql.sys | *THISISNOTAVALIDPASSWORDTHATCANBEUSEDHERE | caching_sha2_password | localhost |
| debian-sys-maint | *8486437DE5F65ADC4A4B001CA591363B64746D4C | caching_sha2_password | localhost |
| phpmyadmin | *5FD2B7524254B7F81B32873B1EA6D681503A5CA9 | caching_sha2_password | localhost |
+------------------+-------------------------------------------+-----------------------+-----------+
5 rows in set (0.00 sec)
You can see from this output that the root user will authenticate using a password. You can now log in to the phpMyAdmin interface as your root user with the password you’ve set for it here.
Configuring Password Access for a Dedicated MySQL User
Alternatively, some may find that it better suits their workflow to connect to phpMyAdmin with a dedicated user. To do this, open up the MySQL shell once again:
- sudo mysql
If you have password authentication enabled for your root user, as described in the previous section, you will need to run the following command and enter your password when prompted in order to connect:
- mysql -u root -p
From there, create a new user and give it a strong password:
- CREATE USER 'sammy'@'localhost' IDENTIFIED WITH caching_sha2_password BY 'password';
Note: Again, depending on what version of PHP you have installed, you may want to set your new user to authenticate with mysql_native_password instead of caching_sha2_password:
- ALTER USER 'sammy'@'localhost' IDENTIFIED WITH mysql_native_password BY 'password';
Then, grant your new user appropriate privileges. For example, you could grant the user privileges to all tables within the database, as well as the power to add, change, and remove user privileges, with this command:
- GRANT ALL PRIVILEGES ON *.* TO 'sammy'@'localhost' WITH GRANT OPTION;
Following that, exit the MySQL shell:
- exit
You can now access the web interface by visiting your server’s domain name or public IP address followed by /phpmyadmin:
https://your_domain_or_IP/phpmyadmin
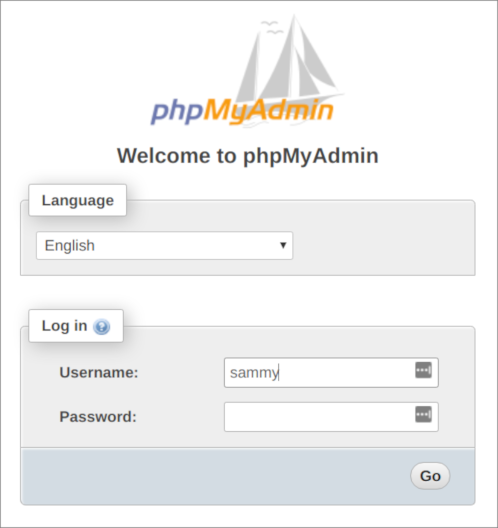
Log in to the interface, either as root or with the new username and password you just configured.
When you log in, you’ll see the user interface, which will look something like this:
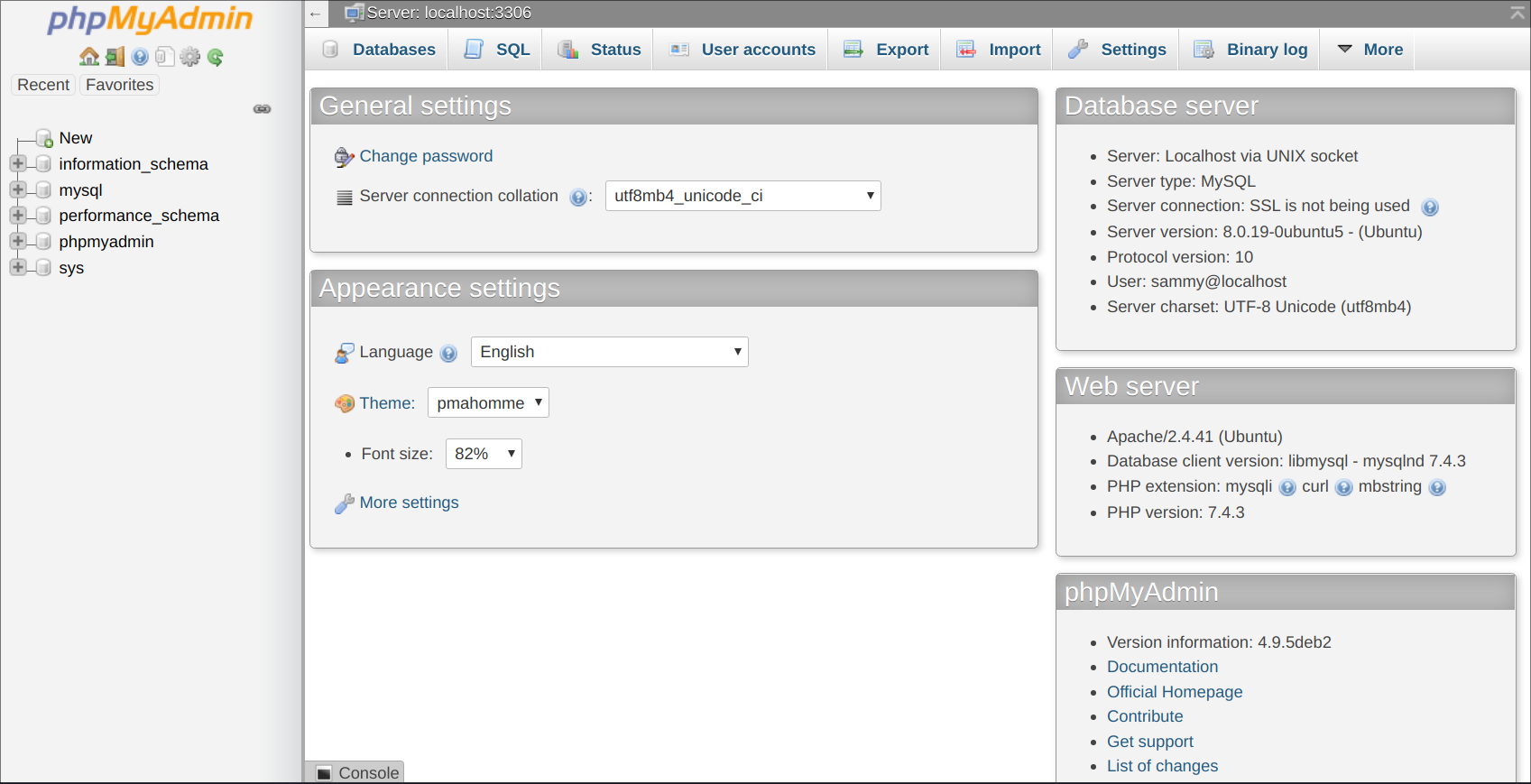
Now that you’re able to connect and interact with phpMyAdmin, all that’s left to do is harden your system’s security to protect it from attackers.
Step 3 — Securing Your phpMyAdmin Instance
Because of its ubiquity, phpMyAdmin is a popular target for attackers, and you should take extra care to prevent unauthorized access. One way of doing this is to place a gateway in front of the entire application by using Apache’s built-in .htaccess authentication and authorization functionalities.
To do this, you must first enable the use of .htaccess file overrides by editing your phpMyAdmin installation’s Apache configuration file.
Use your preferred text editor to edit the phpmyadmin.conf file that has been placed in your Apache configuration directory. Here, we’ll use nano:
- sudo nano /etc/apache2/conf-available/phpmyadmin.conf
Add an AllowOverride All directive within the <Directory /usr/share/phpmyadmin> section of the configuration file, like this:
<Directory /usr/share/phpmyadmin>
Options SymLinksIfOwnerMatch
DirectoryIndex index.php
AllowOverride All
. . .
When you have added this line, save and close the file. If you used nano to edit the file, do so by pressing CTRL + X, Y, and then ENTER.
To implement the changes you made, restart Apache:
- sudo systemctl restart apache2
Now that you have enabled the use of .htaccess files for your application, you need to create one to actually implement some security.
In order for this to be successful, the file must be created within the application directory. You can create the necessary file and open it in your text editor with root privileges by typing:
- sudo nano /usr/share/phpmyadmin/.htaccess
Within this file, enter the following information:
AuthType Basic
AuthName "Restricted Files"
AuthUserFile /etc/phpmyadmin/.htpasswd
Require valid-user
Here is what each of these lines mean:
AuthType Basic: This line specifies the authentication type that you are implementing. This type will implement password authentication using a password file.AuthName: This sets the message for the authentication dialog box. You should keep this generic so that unauthorized users won’t gain any information about what is being protected.AuthUserFile: This sets the location of the password file that will be used for authentication. This should be outside of the directories that are being served. We will create this file shortly.Require valid-user: This specifies that only authenticated users should be given access to this resource. This is what actually stops unauthorized users from entering.
When you are finished, save and close the file.
The location that you selected for your password file was /etc/phpmyadmin/.htpasswd. You can now create this file and pass it an initial user with the htpasswd utility:
- sudo htpasswd -c /etc/phpmyadmin/.htpasswd username
You will be prompted to select and confirm a password for the user you are creating. Afterwards, the file is created with the hashed password that you entered.
If you want to enter an additional user, you need to do so without the -c flag, like this:
- sudo htpasswd /etc/phpmyadmin/.htpasswd additionaluser
Then restart Apache to put .htaccess authentication into effect:
- sudo systemctl restart apache2
Now, when you access your phpMyAdmin subdirectory, you will be prompted for the additional account name and password that you just configured:
https://domain_name_or_IP/phpmyadmin
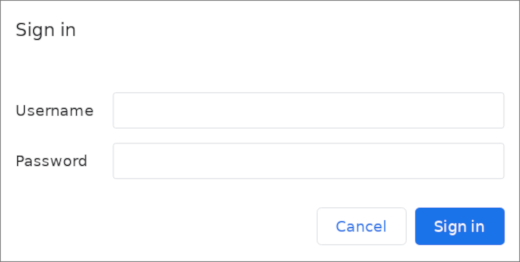
After entering the Apache authentication, you’ll be taken to the regular phpMyAdmin authentication page to enter your MySQL credentials. By adding an extra set of non-MySQL credentials, you’re providing your database with an additional layer of security. This is desirable, since phpMyAdmin has been vulnerable to security threats in the past.
Conclusion
You should now have phpMyAdmin configured and ready to use on your Ubuntu 20.04 server. Using this interface, you can create databases, users, and tables, as well as perform the usual operations like deleting and modifying structures and data.
Get Ubuntu on a hosted virtual machine in seconds with DigitalOcean Droplets! Simple enough for any user, powerful enough for fast-growing applications or businesses.
This textbox defaults to using Markdown to format your answer.
You can type !ref in this text area to quickly search our full set of tutorials, documentation & marketplace offerings and insert the link!






Another excellent walk-through!
The idiosyncrasies that show up in new iterations of apache and php and mysql can catch you by surprise if you haven’t built out a server in a few years.
Thank you so much for this well arranged and logical article.
I followed the instructions here but when I enter "https://mydomain.com/phpmyadmin my browser redirects to an unsecure connection: “http://123.45.67.8/phpmyadmin”.
I’m using “Let’s Encrypt” on my domain, which works fine. But I’ve read that it doesn’t work for IP addresses.
Any solutions?
thank you. I did it. <3
:D What I like DigitalOcean is guide article is best with detail on how to get me walkthrough any technical problem.
Clear and know what the step will be error and get fix. Keep it up.
Mark, would you be able to do a similar guide for a LEMP stack? Cheers
Install phpMyAdmin using the command:
sudo apt update sudo apt install phpmyadminDuring the installation, select “apache2” when prompted to choose a web server.
Configure Apache to recognize phpMyAdmin@localhost by creating a symbolic link:
sudo ln -s /usr/share/phpmyadmin /var/www/html/phpmyadminSecure phpMyAdmin by creating a new user with strong credentials and granting it appropriate privileges:
sudo mysql CREATE USER 'newuser'@'localhost' IDENTIFIED BY 'password'; GRANT SELECT, INSERT, UPDATE, DELETE ON database_name.* TO 'newuser'@'localhost'; FLUSH PRIVILEGES;Edit the phpMyAdmin configuration file to enable HTTPS and restrict access to certain IP addresses or hosts:
sudo nano /etc/phpmyadmin/config.inc.phpAdd the following lines at the end of the file:
$cfg['ForceSSL'] = true; $cfg['Servers'][1]['host'] = 'localhost'; $cfg['Servers'][1]['auth_type'] = 'cookie'; $cfg['Servers'][1]['AllowNoPassword'] = false; $cfg['Servers'][1]['AllowRoot'] = false; $cfg['Servers'][1]['AllowDeny']['order'] = 'deny,allow'; $cfg['Servers'][1]['AllowDeny']['rules'] = array( 'deny from all', 'allow from 192.168.0.1', 'allow from localhost' );Replace “192.168.0.1” with the IP address or hostname of the machines that are allowed to access phpMyAdmin.
Restart Apache for the changes to take effect:
sudo systemctl restart apache2Now you should be able to access phpMyAdmin by going to
https://your-server-name-or-ip/phpmyadminin your web browser, and login using the new user credentials you created.I have followed the tutorial step by step on a wordpress droplet, and I get a 404 page when I load https://URL/phpmyadmin
What did I miss? Thanks
Lovely article. Clear instructions, thks.
Hello !
I followed the tutorial but answered too fast to the “For the server selection, choose apache2” point without reading the WARNING section (even if it was written in red, my fault) How can I start from scratch the procedure ? I tried apt remove with no success…
Thanks !
You can go a step further to avoid script attacks by changing the route to phpmyadmin in /etc/apache2/conf-available/phpmyadmin.conf Just change at the beginning of the file “Alias /phpmyadmin /usr/share/phpmyadmin” by “Alias /yourcustomroute /usr/share/phpmyadmin” Makes it even harder to find and really does not tell attackers what is behind the access point if you use a good name.